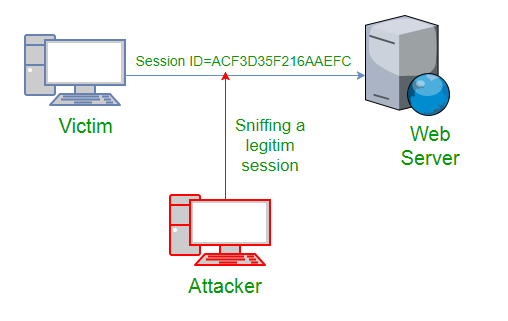
A sniffing attack in system hacking is a form of denial-of-service attack which is carried out by sniffing or capturing packets on the network, and then either sending them repeatedly to a victim machine or replaying them back to the sender with modifications. Sniffers are often used in system hacking as a tool for analyzing traffic patterns in a scenario where performing more intrusive and damaging attacks would not be desirable.
Sniffing Attack:
A sniffing attack can also be used in an attempt to recover a passphrase, such as when an SSH private key has been compromised. The sniffer captures SSH packets containing encrypted versions of the password being typed by the user at their terminal, which can then be cracked offline using brute force methods.
◉ The term “sniffing” is defined in RFC 2301 as: “Any act of capturing network traffic and replaying it, usually for the purpose of espionage or sabotage.”
◉ This definition is not accurate for UNIX-based systems, since any traffic can be sniffed as long as either the attacker has access to network interfaces (NIC) or modifies packets that could not be altered in transit. Sniffing can be performed using a special program like tcpdump, tcpflow, or LanMon that is connected to a port over which the packets can be inspected remotely.
◉ Another sniffing attack called ARP spoofing involves sending forged Address Resolution Protocol (ARP) messages to the Ethernet data link layer. These messages are used to associate a victim machine’s IP address with a different MAC address, leading the targeted machine to send all its traffic intended for the victim through an attacker-controlled host.
◉ This is used to both hijack sessions and also cause flooding of the network via a denial-of-service attack (see Smurf attack).
Every IP packet contains, in addition to its payload, two fields: an IP header, and an Ethernet header encapsulating it.
◉ The combination of these two headers is often referred to as a “packet” by those who work with internet communications. An attacker can, therefore, view and modify an IP packet’s IP header without having to see its payload.
◉ The Ethernet header contains information about the destination MAC address (the hardware address of the recipient machine) and the Ether Type field contains a value indicating what type of service is requested (e.g., precedence or flow control).
◉ The Ether type could be “0xFFFF”, indicating that no service fields were included for the Ethernet frame. This was used in Cisco’s implementation prior to version 8.0.
Key Points:
There are a number of different methods that an attacker can use to perform ARP spoofing. They include:
◉ The attacker has access to the “ARP cache” on their infected machine, which also contains other machines’ MAC addresses, but who do not have or are not using the same IP addresses as other machines with the same MAC addresses in their ARP caches.
◉ The attacker does not know what method the other machines use for keeping a table of MAC addresses, and so simply sets up a network with many duplicate entries.
◉ The attacker sends out forged ARP messages, trying to associate their infected machine with another machine’s MAC address.
Countermeasures:
There are a number of ways that the attacker can be prevented from using these methods, including:
◉ ARP spoofing is not a very effective attack, except in networks that are poorly secured.
◉ In order for an attacker to use this method as a form of masquerading, they must be able to send packets directly to the network (either through access to Wi-Fi or by finding a security flaw). Because of this, the attacker’s IP address is likely to become known very quickly.
◉ A sniffing attack is a form of attack where the attacker tries to access certain data over the network and sniffing is used as an essential task in capturing data. The term “sniffing” comes from the action of sniffing or smelling. The attacker gets hold of this information by using special software called “network analyzer”.
◉ Sniffing in Hacking: it is considered to be an intrusion on your computer system without permission, without your knowledge, and without legal authorization. It’s called hacking, which can be performed by several methods.
Source: geeksforgeeks.org