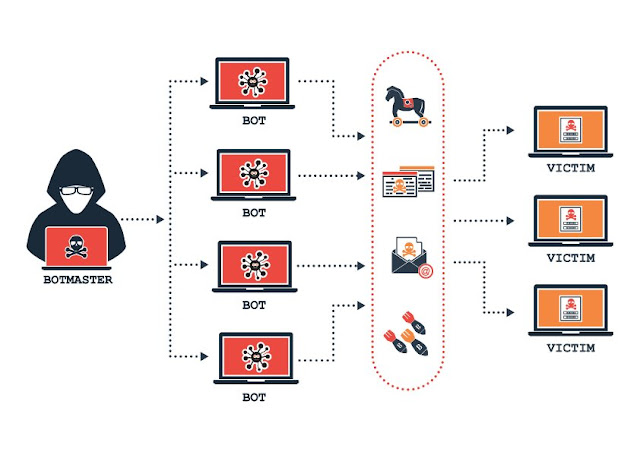
Computer forensics is a high-growth field, with great potential for career progression. Organizations lean on digital forensic analysts to make out and reduce weaknesses to maintain their sensitive information secure. CHFI by EC-Council is one of the most sought-after digital forensic certifications. EC-Council not only evaluates the forensic expertise of the applicants through the CHFI exam, but it also gives on-demand training to the aspiring applicants. CHFI certified professionals are considered experts in executing forensic-related tasks, like evidence collection, intrusion analysis, information recovery, and audit trails maintenance.
What is CHFI Certification?
The CHFI, Computer Hacking Forensic Investigator certification is for professionals in defense and military professionals, systems administrators, legal professionals, banking, e-Business security professionals, insurance, IT managers, and government bodies and police and other law enforcement employees. The CHFI certification will assure that candidates have the essential skills to recognize an intruder's traces and correctly gather the proof needed to prosecute in the court of law. Applicants who can not attend official training must have at least two years of work experience in the Information Security domain to meet the eligibility criteria.Importance of CHFI Certification
Once you pass your CHFI 312-49 certification exam, you may find that you are qualified for a diverse range of jobs. While your prevailing job experience might have qualified you earlier, it is essential to gain a respected certification that proves a commitment to the field, as well as providing strong proof that you have mastered definite areas in Computer forensics.Read: CHFI Certification: How It Can Open Doors and Boost Your Computer Forensics Career
CHFI certification always helps earn immediate respect and qualify you as the professional you are to move forward smoothly and rapidly without having to prove your importance.
Possible Career Paths for CHFI
You can then move your career forward with several distinct brilliant career paths. You can work with law enforcement agencies who are starving for computer investigators. You might look for to work with an organization that finds your particular skillset important to their information technology division. Some of the job profiles that you can take into consideration might involve the following:- Security Engineer
- Digital Forensic Analyst
- Cyber Security Malware Analyst
- Security Auditor
- Security Manager
- Penetration Tester
- Application Security Analyst
- Computer Security Incident Response & Recovery
- Forensics Cyber Weapons and Tactics Advisor
Read: Key Roles of Computer Hacking Forensic Investigator (CHFI): Briefly Explained
How to Prepare for CHFI Certification?
1. Start in Advance
EC-Council CHFI exam is nearly impossible to crack if you do last-minute cramming. Rather, you should start studying before 3-4 months to your scheduled exam date. You're going to be assessed on your skill to read a question, analyze it, and practice concepts. Although most candidates hardly run into questions that at first don't appear to relate to anything they've studied, you can be confused by them if you cram. The CHFI syllabus topics you're being examined on demand a type of understanding that can only be obtained over an organized, thorough course of study—not last-moment, frenzied reviews of study materials.2. Design Study Schedule
To pass the CHFI exam, you need a solid grasp of the concepts and implement them. Besides, you need to practice answering CHFI test questions because the EC-Council certification exams demand you to employ analytical methods to conclude at your answers. Although there are motivated applicants who can design their study schedule effortlessly, it's more probable that you're unsure how or where to begin. Paycheques you receive after passing the CHFI exam are an excellent way to turn doubt into confidence.To prepare for the CHFI certification exam, you can avail plenty of resources online. The cost of study material can depend on what kind of resources you choose. You can choose from books, online courses, online study guides and blogs, practice tests, and online communities.
3. Focus on Taking CHFI Practice Tests
If possible, try to take leave from your job in the last two weeks before the exam for revision and practice tests. Treat the CHFI practicetest as if they are actual exams. Don't get the practice questions in advance. Take time-bound practice tests to get a feel for the time limitations and stress of exam day. You have an average of about 1.6 minutes per CHFI question.Although working on the areas where you scored poorly is essential, don't overlook your more vital CHFI syllabus topics. They need to stay in your mind for long.
4. Have a Game Plan to Stay Calm and Composed on Exam Day
The secret to staying focused and calm while taking the exam is to have a game plan before you sit for the exam. To avoid the last moment rush, be ready early. Don't spend too much time on one question.For the questions that give you difficulty, first reread to understand them. Then, if you still can't conclude to the best answer, try to drop at least one and make a wise guess. Even if you don't have an idea, you should still mark an answer. That's better than leaving it blank because there is no negative marking. Whatever you do, don't frighten if you find several tricky questions in a row. It only makes things more dangerous.
Conclusion
If the world of digital forensic attracts you, if you want to help resolve crimes or discover compromised computer systems, or catch devil employees, then there is no time like the now to begin preparation for the CHFI exam.
There are plenty of job opportunities, and the salaries are usually very high with other types of jobs.
Start studying on your own, take some courses, perform practice tests, achieve your CHFI certificate, and apply for your dream job. It is an interesting and demanding field, but it will require time and effort.