Have you ever wondered what happens when a security incident occurs? How do they figure out what exactly happened, what data (if any) was compromised, and what the follow-up actions are? An incident response analyst’s job is to address all of these issues.
What are cybersecurity incidents?
A cybersecurity incident is a general term that includes security breaches, insider threats, policy violations, external attacks, or a combination of these. They can be either inadvertent or intentional. Either way, proper security incident management needs to be in place. Cybersecurity management is the process of identifying, managing, recording, and analyzing security threats or incidents in real-time.
What is the role of an incident response analyst?
An Incident Response Analyst’s job is to actively monitor systems and networks for intrusions. They identify security flaws and vulnerabilities, perform security audits, risk analyses, network forensics, and penetration tests. They also perform malware analysis and reverse engineering.
Another important role of an incident response analyst is crafting the incident response plan. The incident response plan is a crucial part of any security program. It helps establish and test strategies put in place in the event of a cyber incident to ensure minimal impact. The demand for incident response analysts has been steadily increasing due to the potential vulnerability that cloud services introduce to a system. Because of the world’s increased device usage and storage needs, cloud services are a huge part of how our data is managed. This, unfortunately, increases the threat surface, which invites more computer security incidents, making effective incident response plans mandatory for most organizations.
Drafting an effective incident response plan
When implementing good incident management, you need to be sure to cover all of your bases in terms of prevention, detection, eradication, and recovery. Following the NIST SP 800-61 is a good foundation and the main document that needs to be created is the incident response plan. An incident response plan, or IRP, is a document that outlines what an organization must do in the event of a computer security incident. An IRP also contains a RACI Chart dictating who is responsible for what, who is accountable, who is consulted, and who is informed. Generally, the Computer Emergency Response Team (CERT) is the group that executes the IRP.
But what exactly does the IRP entail? There is a general ruleset that every organization should follow, and then there’s a more in-depth process.
The OODA Loop
The OODA Loop, when broken down, means to Observe, Orient, Decide, and Act. This was created by USAF Colonel John Boyd and can be used by an incident responder to handle live computer security incident handling. The following video gives a brief description:
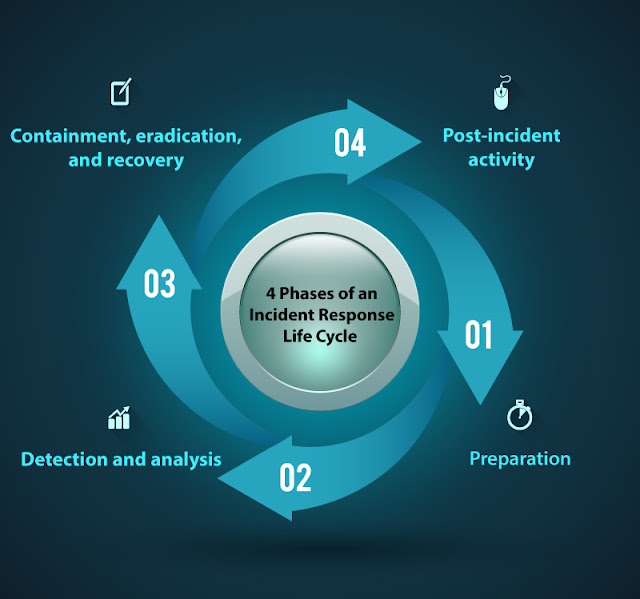
4 Phases of the Incident Response Life Cycle
According to NIST, the incident response lifecycle, or in other words, the incident response process, comprises four phases: preparation, detection and analysis, containment, eradication and recovery, and post-incident activity.
6 Steps in the incident response methodology
The following 6 steps are crucial for a thorough incident response methodology. They cover everything that an incident response analyst should do from preparation and detection to recovery and lessons learned:
1. Preparation
This phase is the workhorse of an incident response plan, and in the end, the most crucial phase to protect the business. This is the phase in which the plan is written and tested.
2. Identification
This is the process where the incident response analyst determines whether the organization has been breached.
3. Containment
Contain the breach so it doesn’t spread and cause further damage to the business. If possible, disconnect affected devices from the Internet. Have short-term and long-term containment strategies ready. It’s also good to have a redundant system back-up to help restore business operations. That way, any compromised data isn’t lost forever.
4. Eradication
Once contained, the incident response analyst must find and eliminate the root cause of the breach. This means all malware should be securely removed, systems should again be hardened and patched, and updates should be applied.
5. Recovery
This is the process of restoring and returning affected systems and devices into the business environment. During this time, it’s important to get all systems and business operations up and running without the fear of another breach.
6. Lessons Learned
Once the investigation is complete, hold an after-action meeting with all Incident Response Team members and discuss what was learned from the data breach by analyzing and documenting everything about the breach. Finally, determine what worked well in the response plan and where there were some holes. Lessons learned from both mock and real events help strengthen systems against future attacks.
How to Become a Certified Incident Handler
“Organizations are looking for professional incident handlers and response personnel who can prepare security policies and plans to tackle incidents with efficacy in time-constrained scenarios in order to reduce the impact of incidents.” -Jay Bavisi, President of EC-Council Group.
Becoming an EC-Council Certified Incident Handler (ECIH) will accomplish just that. The ECIH will teach you the most current techniques in handling attacks; whether it’s as small as a single computer or across an entire network, you will be prepared to stop the attack and prevent future ones. Not only that, but candidates with proper incident response training are more equipped to understand the importance of a timely response and business continuity.
Source: eccouncil.org





0 comments:
Post a Comment