Does your organization have an incident response plan in place in the event an attack occurs? These days, businesses of all levels need to be concerned about security attacks. Cyber attackers are devising new creative techniques and methods, making it arduous to prevent. And DoS attack is one of the most common attacks used by cybercriminals to perpetuate their activities.
What is a DoS attack?
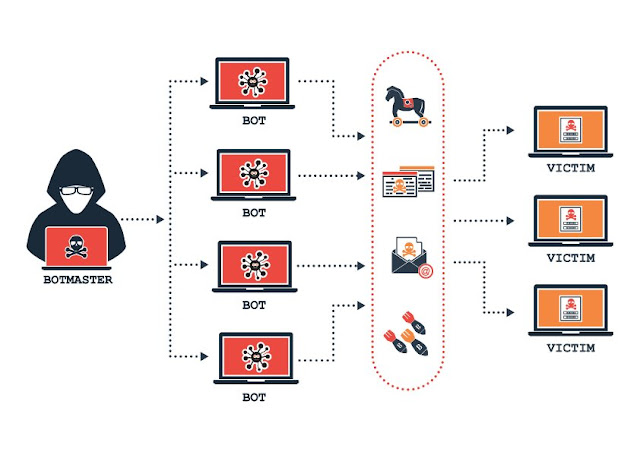
DoS or Denial of Service attack occurs when a legitimate user fails to access devices, information sources, and various other network resources because of a nasty cyber-attack. The attack can impact websites, emails, online accounts, and other services that are dependent on the affected network or computer. A DoS floods the network or host with traffic until the target can respond. At other times, it just crashes and keeps away the rightful user away from accessing his information. Apart from the resources becoming inaccessible, an organization can also lose money due to a DoS attack. That if how severe an attack of DoS caliber is!
Why do attackers use DoS attacks?
DoS affect several organizations over the internet, and it can hinder regular business operation. However, there are ways to prevent it. To mitigate the risk, the first thing you need to identify is why a DoS attack can happen. Here are some of the common reasons this could occur.
◈ Extortion: The hacker can disrupt the services to profit from it by asking for a payment to restore normalcy.
◈ Competitive Businesses: Cyber-criminals are also known to offer their service to businesses that want to rattle their competitors’ operations.
◈ Fights Between Online Individuals and Groups: At times, online rival gangs can use DoS attacks to pull apart each other’s operations and infrastructure. This can cause legitimate businesses to be held in the crossfire.
◈ Self-Induced: Service disruptions and downtime can be due to a non-harmful action made by the organization’s employees mistakenly.
◈ No Reason: At times, several DoS victims fail to learn the apparent reason behind the attack.
How Does DoS attack Work?
Typically, the DoS attack takes advantage of an inherent vulnerability in by understanding how a computer network communicates. There are two methods of DoS attacks, flooding, and crashing services. The recent attack occurs when a system experiences heavy traffic that becomes difficult for the server to buffer. This eventually slows down the system. The next attack exploits the vulnerabilities causing the service or the target system to crash.
How Do You Stop a DoS attack?
Here are a few steps that will help in preventing a DoS attack.
1. Add DoS prevention to your response plan
DoS attacks are deliberately targeted towards unwitting businesses, and it occurs daily. For this reason, you must incorporate DoS mitigation into your cyber incidence response plan to prepare and be on the defensive side of a possible attack.
2. Think like attackers
As you’re planning on developing a DoS mitigation into your response plan, it is good to prepare and think like an attacker. Most times, DoS attackers would change attack routes once they notice you’re blocking their efforts. Therefore, ensure you protect all infrastructures against vulnerabilities and think ahead of attackers.
3. Improve on bandwidth capacity
To make the organization’s infrastructure DoS resistant, you need to make sure you have enough bandwidth. This helps in handling the increased traffic.
4. Spread data across several networks
Spread your server across several data centers and make sure it has a sound traffic balancing system to distribute traffic. This will keep the attacker away from launching a successful DoS attack.
5. Deploy DoS solution ahead of time
Emergency DoS prevention solution is typically deployed within an hour or less. Sometimes, it could take longer to deploy a DoS mitigation solution. Because of this, it is best to have it prepared right before any attack befall.
Cyber incident response plan for a DoS attack
To handle a DoS attack, you can follow these tips.
◉ Sometimes, it may be too late for your security staff to recognize an attack in the traffic log stop the damage. Hence, it would be best to look for tools that are going to automate the entire process and let you know when an incident is taking place.
◉ If there is a DoS attack, it might not be safe to use the company’s networks. However, this can be a problem if the data violation plan is a file that you have saved on the hard drive, and you can only access it through the company’s intranet. So, create a jump bag that will contain a laptop with the required forensic software, USB drives, a contact list of the team members, and tools for detecting, containing, eradicating, and recovering from the incident.
◉ Another necessary cybersecurity incident response is to check if any employee is using a technology or cloud service that the IT team is not aware of. If so, your plan needs to be to respond to the security threats caused by them.
When there is an attack, make sure you don’t forget about the other assets, hosts, and services that present in your network.
Source: eccouncil.org





0 comments:
Post a Comment