With over 2.5 million terabytes of data generated every single day, it is undeniable to predict that future business decisions will solely rely on these chunks of data. In order to fine-tune business processes and to know the behavior of customers, decision makers are already lining up a set of technologies and procuring solutions to perform data analysis on a larger level to pre handedly strategize their marketing and operation decisions.
In addition, the wide array of applications that processes this data is seeking the urgent need for security among businesses. From financial data to personal details of customers, all types of data is transacted and viewed through online web applications. This makes it critical for web applications to stay secure and immune to cyber-attacks.
Read More: 312-76: EC-Council Disaster Recovery Professional (EDRP v3)
To understand how secure these web applications are, organizations need to identify security gaps that are left behind during the web application development process. They also need to discover security misconfigurations or exploitable vulnerabilities that can potentially invite a serious data breach.
A meticulous web application security testing can find all these gaps along with hidden vulnerable points in an application that runs the risk of getting exploited by a hacker. A complete security test allows an organization to detect security loopholes and cyber threats both internally and externally. It also lets you make an informed decision towards putting your security plan.
Let’s now dig deep into why web application security is required and what are the steps to carry out web application security testing.
Why is web application security testing required?
With the spike in web-based applications, cyber crimes became commonplace. Over 2,000 confirmed data breaches that took place in 2019 and several hundred in 2020 paint a rather grim picture for web security. These data breaches were impactful and caused businesses to not only lose data but also revenue and business reputation.
The most common factor linked to data breaches was either business delaying identifying vulnerabilities in their applications or not implementing a risk assessment for their internal operations.
As far as the need for security for web applications is concerned, here are a couple more reasons why web application security testing is required for businesses:
1. Errors in programming invite hackers
Cybercriminals often spend a considerable amount of time to find vulnerable areas in an application and that leads them to bugs crept in during programming. Errors such as improper file permissions, unchecked input fields, and insecure admin folders, or any other misconfigurations allow attackers to use methods like code injection and account takeover very easily.
2. Security flaws create obstruction
Going back to the drawing boards repeatedly due to security concerns leads to a lot of precious time loss that could be used in productive activities. If security is considered as an afterthought, it does not fully encompass all areas of an application. Security infused and tested during each software development cycle can change this.
Developers should also check on the overall security infrastructure and investigate weak spots with every update in the application to improve performance and efficiency. This is an alternate way to embed security into the application itself rather than implementing it as an add-on. Patching security flaws during the SDLC (Software Development Lifecycle) is the ideal way to keep a check on the security of the application. It becomes time-taking and complex if left for later.
Steps in web application security testing
1. Gathering information
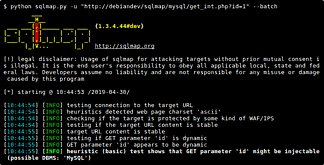
The reconnaissance phase is a crucial part of a security analysis since it helps in uncovering vulnerabilities and exposing areas requiring a revamp. Testers then use this information to conduct further testing. In passive reconnaissance, testers gather information about the system without actually interacting with it. This information is generally public knowledge that can be gathered by simple searches. Whereas, in active reconnaissance, testers probe the application using various tools to gather details. Below are some tools and their usage:
◉ Nmap: Nmap network scanner helps in fingerprinting an application, by gathering details like OS, software, a scripting language used by the server, also any open ports and services running.








0 comments:
Post a Comment